Malware Can Steal Data From Non Networked Computers, Via Heat
Malware Can Steal Data From Non Networked Computers. Back in 1999, Neal Stephenson’s novel Cryptonomicon introduced me to the idea of Van Eck phreaking—intercepting the weak electromagnetic radiation from a computer monitor to recreate what the person is seeing on the screen.
Now security researchers have come up with an exploit that uses an even simpler form of radiation: heat. BitWhisper, as researchers Mordechai Guri and Professor Yuval Elovici of Ben-Gurion University’s Cyber Security Research Center have dubbed their program, targets air-gapped machines—computers that are not physically (or wirelessly) connected to the Internet. By using malware that can tap into computers’ cooling systems and temperature sensors, the hack can send information back and forth between two adjacent machines.

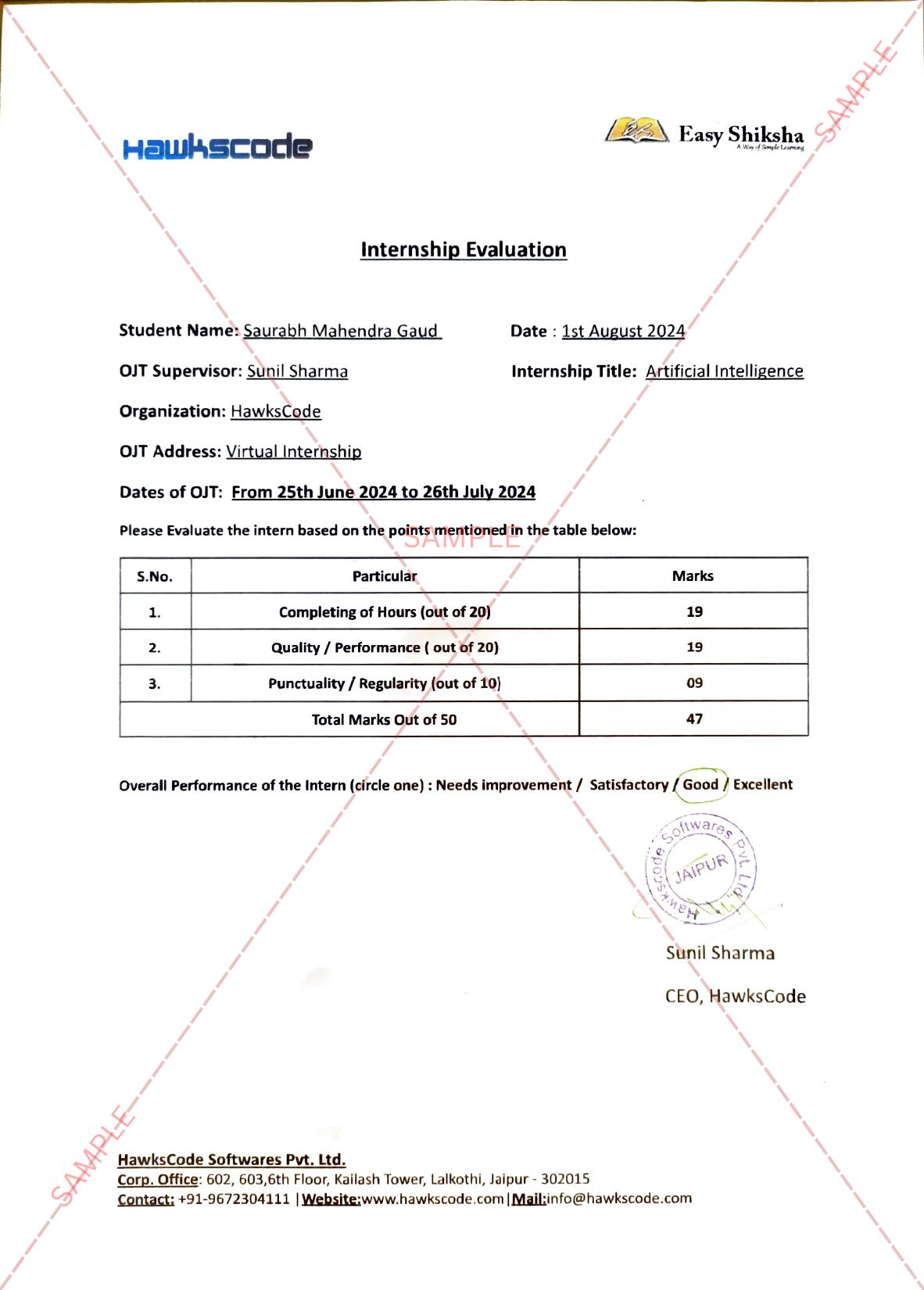
Important Announcement – EasyShiksha has now started Online Internship Program “Ab India Sikhega Ghar Se”
For example, raising the temperature of one computer by a single degree over a specified time period would be detected by the adjacent computer as a binary bit of ‘1’; returning it to the baseline temperature would be interpreted as a ‘0.’ String enough of those together and they can represent a computer command or raw data, such as a password.Malware Can Steal Data From Non Networked Computers.
Naturally, there are a host of caveats. In order to work, the two computers need to be just 15 inches apart (close enough to detect the changes in heat), one needs to be connected to the internet, and they both have to be infected with the malware. And given the time inherent in raising and lowering temperatures, sending data takes a long time–potentially hours.
Top Courses in Software Engineering
This isn’t the first attempt to target air-gapped computers. The Stuxnet worm largely thought to have been developed by the U.S. National Security Agency and Israel jumped from computer to computer via compromised USB drives. Researchers have also come up with ways to transmit information between hacked computers using their built-in speakers to generate high-frequency sounds that can be heard by microphones but not ears. And Guri himself previously came up with an exploit called AirHopper that could transmit information as FM signals to nearby compromised mobile phones, which would then send that data on to the outside world.Malware Can Steal Data From Non Networked Computers.
As tempted as you may be to look askance at your computer the next time its fans kick on, don’t worry too much: it’s probably just running hot as it processes your high-def stream of House of Cards. Probably.
Empower your team. Lead the industry
Get a subscription to a library of online courses and digital learning tools for your organization with EasyShiksha
Request NowQ. Are EasyShiksha's internships truly free?
Yes, all internships offered by EasyShiksha are completely free of charge.
Q. How can I apply for an internship with EasyShiksha?
You can apply by visiting our website, browsing available internships, and following the application instructions provided.
Q. What types of internships are available through EasyShiksha?
EasyShiksha offers a wide range of internships across technology, business, marketing, healthcare, and more. Opportunities are continuously updated.
Q. Will I receive a certificate upon completing an internship?
Yes, upon successful completion, you will receive a certificate recognizing your participation and achievements.
Q. Are EasyShiksha's internship certificates recognized by universities and employers?
Yes, the certificates are recognized by universities, colleges, and employers worldwide.
Q. Is the download of certificates free or paid?
Access to internships and courses is free, but there is a small fee to download certificates, covering administrative costs.
Q. When can I start the course?
You can choose any course and start immediately without delay.
Q. What are the course and session timings?
These are fully online courses. You can learn at any time and pace. We recommend following a routine, but it depends on your schedule.
Q. What will happen when my course is over?
After completion, you will have lifetime access to the course for future reference.
Q. Can I download the notes and study material?
Yes, you can access and download course materials and have lifetime access for future reference.
Q. What software/tools would be needed for the course?
All necessary software/tools will be shared during the training as needed.
Q. I’m unable to make a payment. What should I do?
Try using a different card or account. If the problem persists, email us at info@easyshiksha.com.
Q. Do I get the certificate in hard copy?
No, only a soft copy is provided, which can be downloaded and printed if required.
Q. The payment got deducted but shows “failed”. What to do?
Technical errors may cause this. The deducted amount will be returned to your account in 7-10 working days.
Q. Payment was successful but dashboard shows ‘Buy Now’?
Sometimes payment reflection is delayed. If it takes longer than 30 minutes, email info@easyshiksha.com with the payment screenshot.
Q. What is the refund policy?
If you face technical issues, you can request a refund. No refunds are issued once the certificate has been generated.
Q. Can I enroll in a single course?
Yes, select the course of interest, fill in the details, make payment, and start learning. You will also earn a certificate.
Q. My questions are not listed above. I need further help.
Contact us at info@easyshiksha.com for further assistance.
I hope you understand this blog, Malware Can Steal Data From Non Networked Computers.
For more information related to technology, visit: HawksCode and EasyShiksha
ALSO READ: why-you-should-use-react-native-to-program-your-app
Get Course: management-leadership-skills-Know-when-to-manage-or-lead