Europe’s supercomputers hijacked by attackers for crypto mining
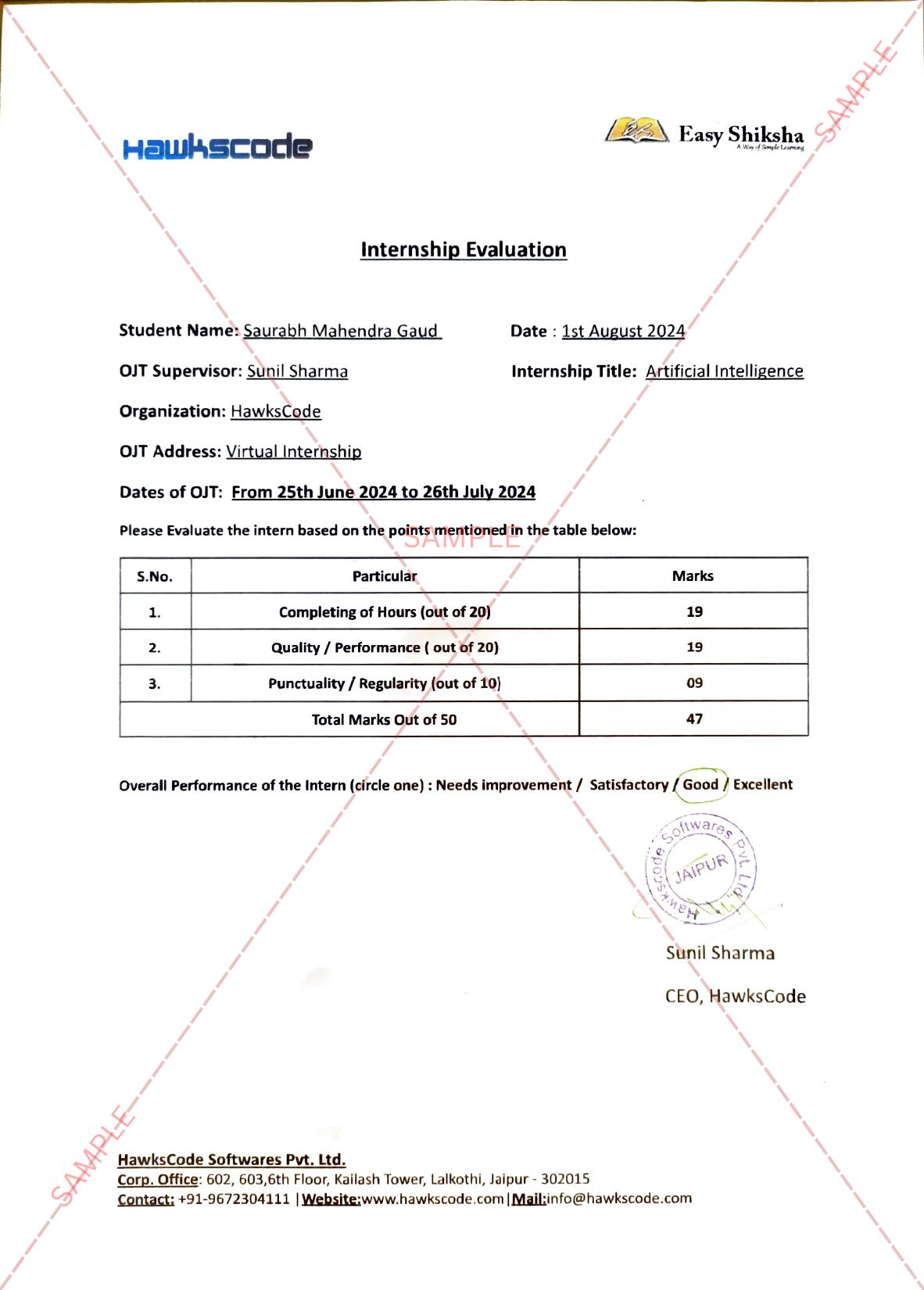
Supercomputers hijacked by attackers for crypto mining. At least a dozen supercomputers across Europe have shut down after cyber-attacks tried to take control of them. “A security exploitation” disabled access to the Archer supercomputer, at the University of Edinburgh, on 11 May. A pan-European supercomputing group says they tried to use the machines to mine cryptocurrency.
Staff said they were working with the National Cyber Security Centre to restore the system, which had recently installed a pandemic modelling tool.

Important Announcement – EasyShiksha has now started Online Internship Program “Ab India Sikhega Ghar Se”
“We now believe this to be a major issue across the academic community as several computers have been compromised in the UK and elsewhere in Europe,” the team said.
The NCSC said: “We are aware of this incident and are providing support.
“The NCSC works with the academic sector to help it improve its security practices and protect its institutions from threats.”
Also on 11 May, another attack shut down five supercomputers in Germany. Others followed elsewhere in Germany in the following days, as well as in Switzerland, and reportedly Barcelona.
Top Courses in Software Engineering
They exploited an Secure Shell (SSH) connection, which academic researchers use to log in to the system remotely.
And once inside, the attackers appear to have deployed cryptocurrency-mining malware.
The security team at the European Group Infrastructure foundation said: “A malicious group is currently targeting academic data centres for CPU [central processing unit] mining purposes.
“The attacker is hopping from one victim to another using compromised SSH credentials.”
Empower your team. Lead the industry
Get a subscription to a library of online courses and digital learning tools for your organization with EasyShiksha
Request NowQ. Are EasyShiksha's internships truly free?
Yes, all internships offered by EasyShiksha are completely free of charge.
Q. How can I apply for an internship with EasyShiksha?
You can apply by visiting our website, browsing available internships, and following the application instructions provided.
Q. What types of internships are available through EasyShiksha?
EasyShiksha offers a wide range of internships across technology, business, marketing, healthcare, and more. Opportunities are continuously updated.
Q. Will I receive a certificate upon completing an internship?
Yes, upon successful completion, you will receive a certificate recognizing your participation and achievements.
Q. Are EasyShiksha's internship certificates recognized by universities and employers?
Yes, the certificates are recognized by universities, colleges, and employers worldwide.
Q. Is the download of certificates free or paid?
Access to internships and courses is free, but there is a small fee to download certificates, covering administrative costs.
Q. When can I start the course?
You can choose any course and start immediately without delay.
Q. What are the course and session timings?
These are fully online courses. You can learn at any time and pace. We recommend following a routine, but it depends on your schedule.
Q. What will happen when my course is over?
After completion, you will have lifetime access to the course for future reference.
Q. Can I download the notes and study material?
Yes, you can access and download course materials and have lifetime access for future reference.
Q. What software/tools would be needed for the course?
All necessary software/tools will be shared during the training as needed.
Q. I’m unable to make a payment. What should I do?
Try using a different card or account. If the problem persists, email us at info@easyshiksha.com.
Q. Do I get the certificate in hard copy?
No, only a soft copy is provided, which can be downloaded and printed if required.
Q. The payment got deducted but shows “failed”. What to do?
Technical errors may cause this. The deducted amount will be returned to your account in 7-10 working days.
Q. Payment was successful but dashboard shows ‘Buy Now’?
Sometimes payment reflection is delayed. If it takes longer than 30 minutes, email info@easyshiksha.com with the payment screenshot.
Q. What is the refund policy?
If you face technical issues, you can request a refund. No refunds are issued once the certificate has been generated.
Q. Can I enroll in a single course?
Yes, select the course of interest, fill in the details, make payment, and start learning. You will also earn a certificate.
Q. My questions are not listed above. I need further help.
Contact us at info@easyshiksha.com for further assistance.
Jamie Akhtar, chief executive of UK security company Cybersmart, said: “Universities are home to some of the most advanced research projects in the world across many disciplines – including computer science – but they are also notoriously vulnerable to attack if they are connected to the wider university network.”
I hope you like this blog, Supercomputers hijacked by attackers for crypto mining. To learn more visit HawksCode and Easyshiksha.
ALSO READ: chemistry-breakthrough-could-speed-up-drug-development
Get Course: autodesk-fusion-360-robot-and-cad-designer